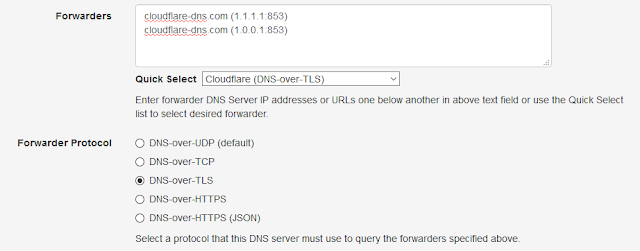
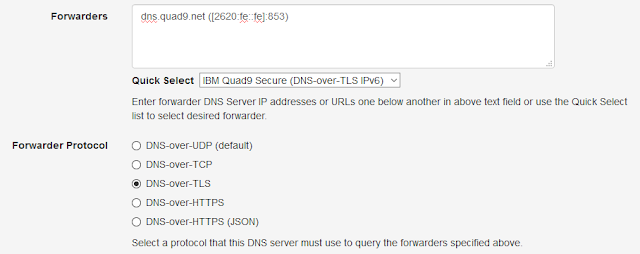
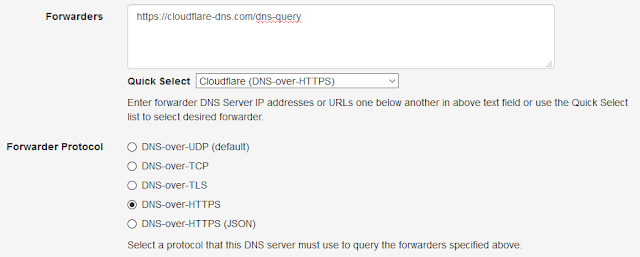
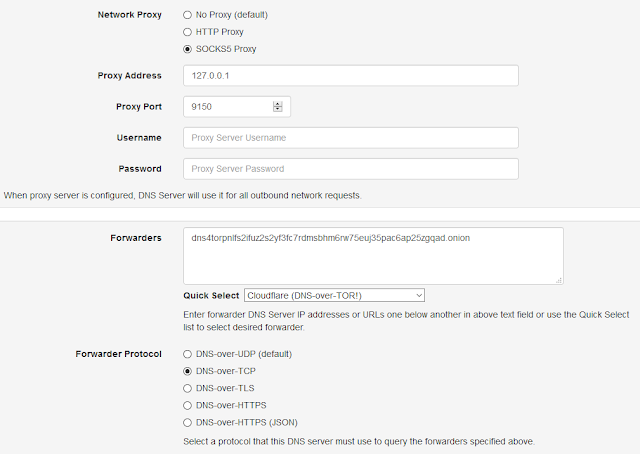
Technitium Mesh, a successor to the Bit Chat project, has been released and is available to download directly from the Mesh website.
 |
| Technitium Mesh |
Introduction
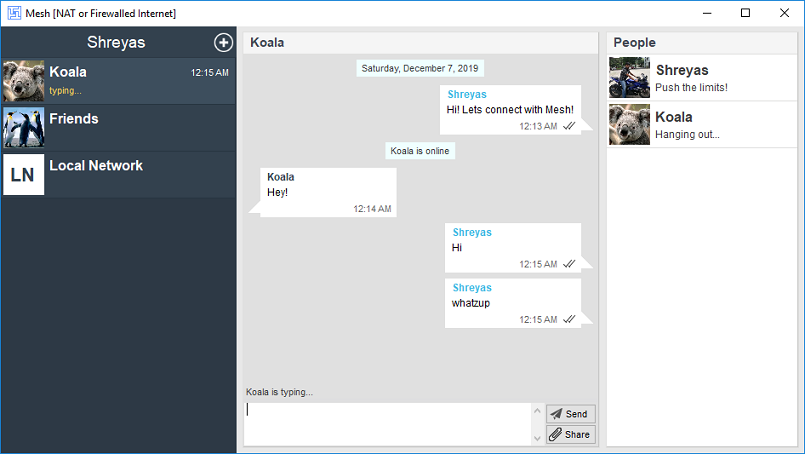
Mesh is a secure, anonymous, peer-to-peer (p2p), open source instant messenger that provides end-to-end encryption with Perfect Forward Secrecy (PFS). Mesh can be used on the Internet or on offline private LAN networks for private messaging, group messaging and file transfers. Mesh is based on Bit Chat and retains it core concepts but has some major changes.Unlike Bit Chat, Mesh does away with centralized user profile registration based on email address. Instead, users now can create multiple local profiles that can be used simultaneously and require to use a generated User Id. This major change was decided based on many people unwilling to disclose their email address or accused Technitium of harvesting email addresses. To be clear, Technitium never used the collected email addresses provided during the profile registration process to even inform existing users that the Bit Chat project is closing its operations.
The generated Mesh User Id is required to be exchanged to initiate private chat and can be changed anytime to avoid previously used User Id from being abused by anyone to stalk or harass you. Even when joining a group chat, a new User Id is generated each time so that the User Id disclosed in group chat cannot be used to initiate a private chat invitation. This makes sure that you are in total control over who is allowed to initiate private chat invitations and when.
The User Id is generated using an algorithm that uses RSA public key linked to the user profile and a random number. This algorithm allows each peer to authenticate the other peer during the peer-to-peer connection process to ensure their identity.
Mesh also removes the use of BitTorrent trackers that were being used by Bit Chat. Using torrent trackers created connectivity issues since many ISPs around the globe use deep packet inspection to block BitTorrent traffic. This also affected Bit Chat since ISPs could not differentiate between both the applications and blocked any traffic that was found using torrent trackers. Instead, Mesh now completely relies on Distributed Hash Tables (DHT).
Mesh now allows creating anonymous profiles that use Tor Network. Mesh includes Tor binaries to allow the app to use Tor Network anytime its necessary. Anonymous profiles and peer-to-peer (p2p) profiles are the two type of profiles that are now available. Both the profiles are interoperable such that a p2p profile user can communicate with anonymous profile user using the built in Tor support. This interoperability means that you can have a group where both p2p users and anonymous users can join together. Anonymous profiles use Tor hidden service to accept inbound connection requests but use a new hidden service onion domain name each time the user logs in to the profile to avoid being tracked using the onion domain name.
Read more technical details on the Frequently Asked Questions (FAQ) page.
Features
- Completely decentralized, peer-to-peer architecture that works even on offline private LAN networks. No centralized profile registration is needed.
- End-to-end encryption with Perfect Forward Secrecy (PFS).
- Allows you to create anonymous profiles that use Tor Network.
- Multiple profile support allows you to create many profiles and use all of them simultaneously.
- Allows creating private chat and group chat with file transfer support.
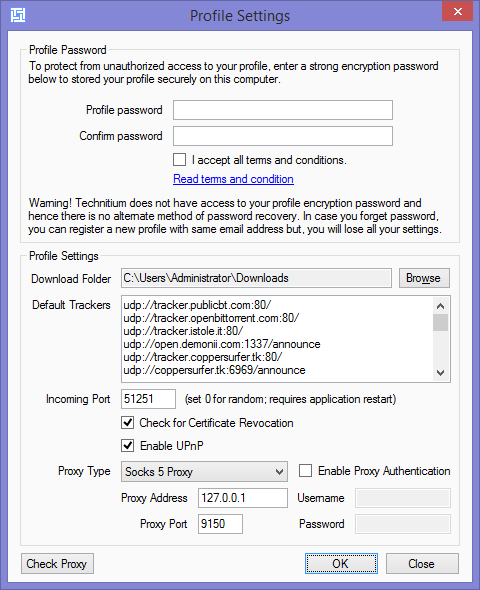
- User profiles are stored locally using strong encryption protected by passphrase.
- Works peer-to-peer with IPv4 as well as IPv6 networks.
- Automatic port forwarding using your router's UPnP feature.
Open Source
Mesh is open source and source code is available under GNU General Public License v3 on GitHub. The software code is made open source to increase confidence in the security that we intend to provide.