While, DoH is a really interesting feature to have from privacy perspective, it is Firefox's implementation that is a bit controversial. Firefox has deal with two public DNS providers, Cloudflare and NextDNS, in its Trusted Recursive Resolver (TRR) program which lists these providers directly into the web browser's DoH options. The controversy is Firefox enabling DoH for users automatically with an opt-out policy.
Not just Firefox but, Google Chrome and Microsoft Windows 10 is also implementing DoH support. Google Chrome's approach is a bit different from Firefox. Chrome will upgrade to use DoH protocol if you are already using a public DNS provider that supports DoH protocol. Microsoft is experimenting with a similar DoH upgrade approach with Windows 10 insider builds.
Firefox's opt-out policy bypasses the local network policies by not using the DNS servers provided by the network administrators. This creates headache for network administrators who wish to keep track or filter DNS traffic for security or other reasons. This is an issue even with people who use DNS based filtering software on their home network.
To help network administrators, Firefox has introduced a Canary domain to disable DoH on their networks. Using this canary domain (use-application-dns.net), a network administrator can signal Firefox on their networks to disable the automatic switch to DoH. However, its important to note that if a user configures DoH manually, then the canary domain signal is ignored by the web browser.
Note: The canary domain only applies to users who have DoH enabled as the default option. It does not apply for users who have made the choice to turn on DoH by themselves.To disable DoH on your network, you need to either block the canary domain entirely such that the DNS server responds with a NXDOMAIN response code or that the server returns an empty response with no A or AAAA records.
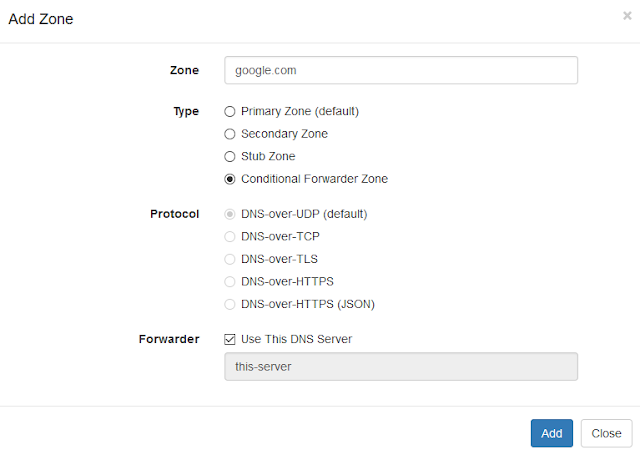
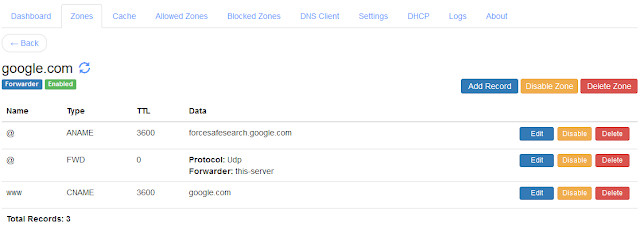
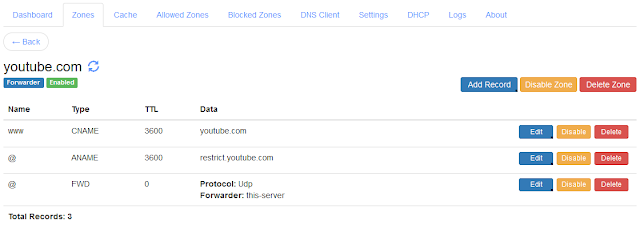
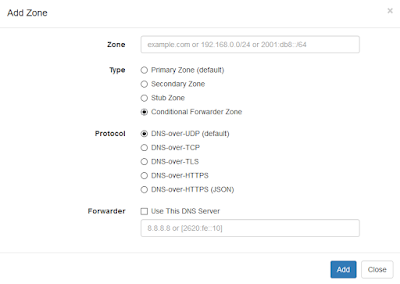
You can do this configuration on your Technitium DNS Server setup by simply adding an empty zone for the canary domain. The zone once added must look like as shown in the screenshot below:
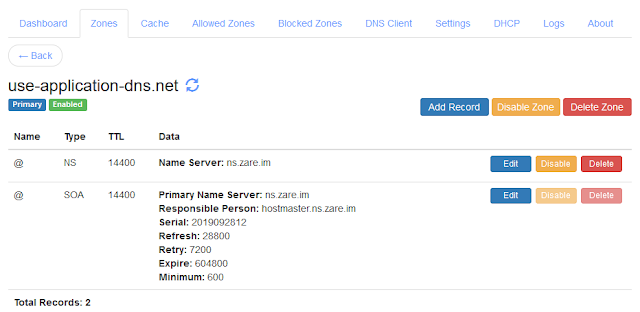 |
| Firefox Canary Domain Zone Configuration |
Let me know if you have any queries in the comments below or send an email to support@technitium.com.