With the release of Technitium DNS Server version 1.3 which adds support for DNS-over-TLS & DNS-over-HTTPS forwarders, it is now a good solution to be used by anyone concerned with privacy & security for domain name resolution on their Internet connection for Windows 10, Linux or macOS.
If you are not clear about what DNS is then read on. Domain Name System (DNS) is a decentralized system that allows you to find out the Internet Protocol (IP) address of any website (like www.technitium.com). So, when you enter a website domain name into your web browser, the web browser uses DNS to find out the IP address of that website. Once the IP address is known, the web browser can then connect to the web server on that IP address using TCP/IP protocols and download webpages and other embedded resources to display on to your screen. DNS servers don't just store IP address records but also store different types of records like mail exchange (MX) records which tell email servers where to deliver email for the recipient user of a given domain.
DNS servers and client use UDP or TCP protocol to exchange requests and responses which are not encrypted. This allows anyone on the network to see those requests and even hijack requests by sending back spoofed responses. There have been many instances reported in media of DNS hijacking done by malware, hacked home wifi routers or even by many Internet Service Providers (ISPs). ISPs in certain places have been found to redirect users to "custom" search pages instead of Google Search or even blatantly injecting Ads on websites that are not using HTTPS security. In some countries, ISPs often use their DNS servers to block websites to enforce government censorship orders.
To mitigate these issues, DNS-over-TLS and DNS-over-HTTPS protocols have been developed and are currently available to be used by a few DNS providers notably Cloudflare, Google and Quad9. But, currently, no operating system, applications or web browsers have built in support for these protocols.
With Technitium DNS Server installed on your computer (or on your network), you can make all your applications indirectly use these DNS providers with the new secure protocols hiding all your DNS traffic from your ISP. Lets see how to configure the DNS Server to use these services to take control and secure domain name resolution on your computer or private networks.
Technitium DNS Server is not configured out-of-the-box with these settings since you have to make a choice yourself of which DNS provider to use. All public DNS providers have their own privacy policies that you must understand before choosing it.
Cloudflare privacy policy promises that DNS query logs are only maintained for 24 hours with not personally identifiable data. They also promise to not sell the data to 3rd parties.
Google's privacy policy claims to maintain a temporary log for 24 to 48 hours which contains user's full IP address details. And a permanent log which redacts the personally identifiable data. There are no details mentioned how this data is used or whom its shared with.
Quad9's privacy policy promises that they do not keep any logs but, only anonymized statistical data on specific domain names which contains things like domain name, timestamp, geolocation, total hits, etc.
Below is a list of DNS providers grouped by the protocol they support. You can configure one or more DNS providers as forwarders but they must use the same protocol.
DNS-over-TLS protocol providers:
- Cloudflare IPv4 {cloudflare-dns.com (1.1.1.1:853), cloudflare-dns.com (1.0.0.1:853)}
- Cloudflare IPv6 {cloudflare-dns.com ([2606:4700:4700::1111]:853), cloudflare-dns.com ([2606:4700:4700::1001]:853)}
- Google IPv4 {dns.google (8.8.8.8:853), dns.google (8.8.4.4:853)}
- Google IPv6 {dns.google ([2001:4860:4860::8888]:853), dns.google ([2001:4860:4860::8844]:853)}
- Quad9 Secure IPv4 {dns.quad9.net (9.9.9.9:853)}
- Quad9 Secure IPv6 {dns.quad9.net ([2620:fe::fe]:853))
DNS-over-HTTPS protocol providers:
- Cloudflare (https://cloudflare-dns.com/dns-query)
- Google (https://dns.google/dns-query)
- Quad9 Secure (https://dns.quad9.net/dns-query)
DNS-over-HTTPS (JSON) protocol providers:
- Cloudflare (https://cloudflare-dns.com/dns-query)
- Google (https://dns.google/resolve)
- Quad9 Secure (https://dns.quad9.net/dns-query)
To make the configuration quick, easy and error free, there is Quick Select drop down list available which lists all the above options. Just selecting the desired option in the Quick Select list will populate the settings automatically for you.
See these examples below to know how the configuration looks like:
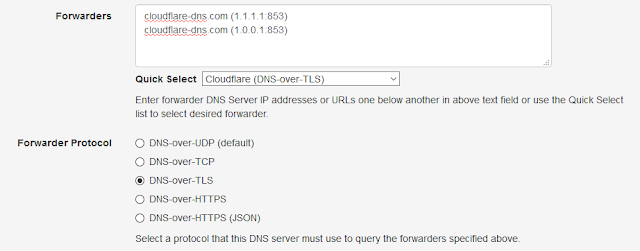 |
| DNS-over-TLS Using Cloudflare |
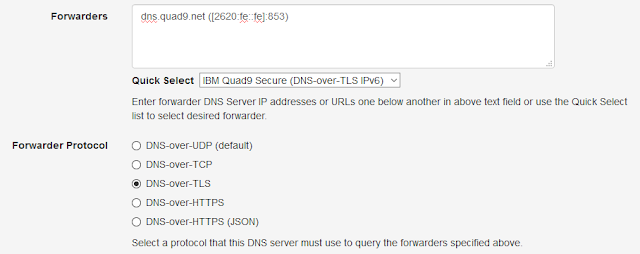 |
| DNS-over-TLS Using Quad9 For IPv6 Internet |
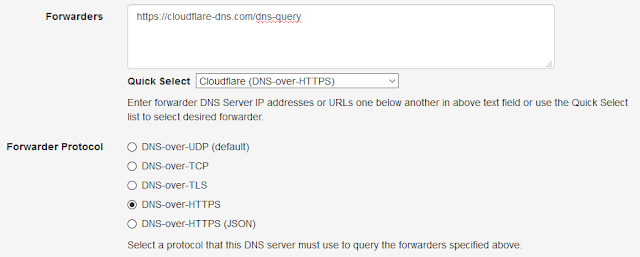 |
| DNS-over-HTTPS Using Cloudflare |
 |
| DNS-over-HTTPS (JSON) Using Google |
As you may have noticed, Cloudflare provides support for all three protocols. Not only that, it is possible to use Cloudflare DNS over Tor hidden service too! Technitium DNS Server v1.3 adds support for configuring proxy server which can of course be made to use Tor running on your computer and use Cloudflare DNS hidden service because WHY NOT?!
You just need to configure dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion hidden service address as forwarder and since all hidden service requests over Tor network are inherently end-to end encrypted, you can use DNS-over-TCP protocol with it. Tor is not included with the software so you will need to install Tor separately and configure it as a SOCKS5 proxy.
This option hides your query from your ISP as well as hides your identity from Cloudflare. But seriously, if you are really that paranoid, just use Tor Browser for all your web browsing.
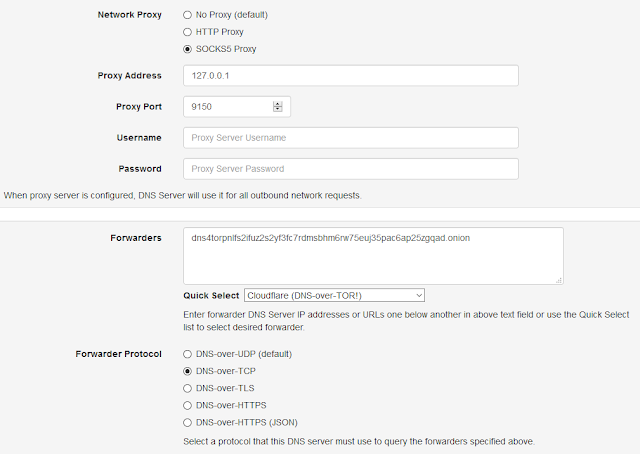 |
| DNS-over-Tor Config For Cloudflare DNS Hidden Service |
Once you have configured forwarders, make use of the DNS Client on the web console to test the setup by making a test query to "this-server". If everything is configured correctly, you will see the IP address for the test domain you entered inside the "Answers" section of the JSON formatted output.
Finally, to make all your computers and applications to use Technitium DNS Server, you need to configure it on your Ethernet or WiFi network adapter. You just need to setup loopback IP address (127.0.0.1 for IPv4 & ::1 for IPv6) as DNS Server in your network adapter settings as shown below:
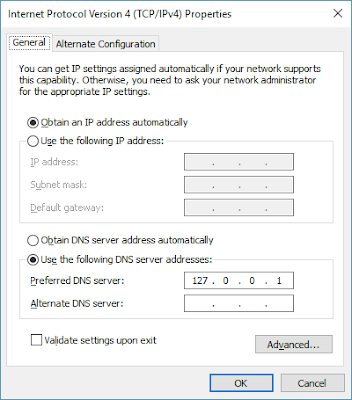 |
| IPv4 DNS Server Network Configuration |
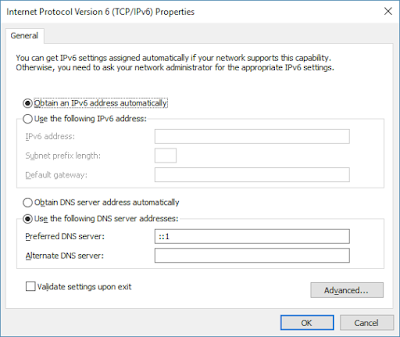 |
| IPv6 DNS Server Network Configuration |
For more queries, write comments below or send an email to support@technitium.com.
can i create my tld on dns server?
ReplyDeleteYes, you can create any domain or TLD on the DNS Server. You can delegate a zone too to specific name servers by creating NS records that point to those servers.
Deletehow to create NS records that point to those servers?
ReplyDeleteYou dont need to create NS records. You just need to configure them as forwarder from the Settings tab.
DeleteIn tab zone?
DeleteThere is a Setting tab to the right end. In there you will need to scroll down a bit and you will find Forwarders textbox. In there, you can use the Quick Select dropdown to select one of the popular public DNS services.
DeleteHow can I point any request to a specific IP? Example, google.com or facebook.com -> 192.168.1.100 (captive portal)
ReplyDeleteYou just need to switch to the Zone tab in the DNS Server web console and add a new zone "google.com". In that zone, add a Type A Record, name as blank or '@' and enter the IP address as the value. You will need to add another CNAME type record with name as 'www' and value as 'google.com. CNAME record will make 'www.google.com' point to 'google.com' and the IP address assigned to 'google.com' will be used automatically.
DeleteDo these steps for any domain you want to redirect to a local web server.
Use the DNS Client tab in the web console to query the zone to confirm if its working correctly.
DeleteThank you for explanation, it was very helpful I appreciate it. But I mean if its possible to point ANY domain request to an specific IP. Whatever user type redirects to my captive portal. Thanks in advance.
DeleteDNS catchall or something like that, pointing every single domain to a specific ip.
ReplyDeleteYou could achieve it using wildcard subdomain entry. For this, you will need to create a zone for each top level domain (TLD) like com, net, org, uk, us, in, etc. Lets say you create a 'com' zone, you can then add a Type A record with name as '*' and value as your local server IP address. This will catch all sub domains for 'com'. Likewise you will need to create a zone for all top level domains. A root level wildcard zone is not supported.
DeletePlease explain PROTOCOLS options from SETTINGS page with example. Also tell what should be the path for TLS certificate file. Can I use self-signed cert for this? What will be the local address for DNSoverTLS and DNSoverHTTPS?
ReplyDeleteThese protocols are optional and only to be enabled if you have specific applications that can use these protocols. Like if you wish to host the DNS Server on a VPS and then use its DNS-over-TLS or DNS-over-HTTPS protocol services with your web browser like Firefox or on your Android Mobile. For usual home network usage, there is no need to enable these protocols.
DeleteIf you wish to use the protocols with public DNS providers like Cloudflare, Google or Quad9 then you need to configure their addresses as forwarder in the settings (at the bottom). You can use the Quick Select dropdown to select popular public DNS providers.
If you want to host your own DNS Server with these protocols then read below:
The TLS Certificate used cannot be self signed if you want the applications to be able to use the service. You can get a free certificate for your domain name using Lets Encrypt and then use the cert with the DNS Server.
The TLS Certificate path in settings is the path where the cert .pfx file is stored on the server. It can be any path on the server where you have the cert files saved. The TLS Certificate password is the .pfx file password. You can create .pfx file from a .crt file using openssl command (just google for the syntax).
The address for DNS-over-TLS will be the TLS certificate domain name combined with port 853: domain-name:853
The address for DNS-over-HTTPS will be TLS certificate domain name as a url: https://domain-name/dns-query
Hi there,
ReplyDeleteI have a question. I just need to solve Server name on the wireless devices..
they access to a intranet webpage like:
https://server01/page.apsx
what i need to do to resolve server01??
thanks in advanced.
Windows does not use DNS to resolve computer names. Instead it will use NBNS, mDNS and LLMNR protocols. If you wish to use DNS names then you can create something like server01.local zone and then configure the webserver with the domain name and then try to use it. Better way is to use the actual production domain name of the website to create zone on the DNS server and then use the enable/disable options on the zone to switch between staging and production.
DeleteThe devices are android.. but the server is windows!
DeleteI install DNS Server on windows with:
Zone: server01
- A @ 192.168.xxx.xxx and TTL 10
Settings:
DNS Server domain: server01
address: 127.0.0.1
::1
with everything default!
the android devices dns to server IP .. but nothing!!
The devices does not know where is the server01!!
Can you help?
You need to make sure that the andriod device is able to resolve IP address. If its not getting the right IP address then you will see DNS_PROBE_FINISHED_NXDOMAIN.
DeleteIf its able to find the address and still you get some other error from web server then make sure your website is using the same domain name or is running as a default website. Also, you need to make sure that the Windows Firewall is configured correctly.
If you are still unable to find the issue then do send screenshot of the error message and details of config to support@technitium.com.
Hey when adding a txt dkim record the following message appears: "Error! Value was either too large or too small for an unsigned byte." Would be great to find a way around it! Otherwise great and easy to use.
ReplyDeleteThis is due to the size limitation of TXT record. The TXT record can contain at max 255 character string. So, for a long DKIM record, you will need to split it into multiple records manually add the TXT records.
DeleteCheck out these links for more details:
https://serverfault.com/questions/255580/how-do-i-enter-a-strong-long-dkim-key-into-dns
http://hack.limbicmedia.ca/how-to-split-dns-dkim-records-properly/
Unfortunately, I must say this did not work for me. Both the ("key1 key2") and the "key1"\"key2" methods ended up breaking my dns records, which forced me to delete the zone and rewrite every entry. Anyone found a way?
Deletehttps://serverfault.com/questions/255580/how-do-i-enter-a-strong-long-dkim-key-into-dns
ReplyDeleteanswered Mar 22 at 19:30 Johannes Winter <- This!
Greetings. Trying to set this up as a local proxy DNS server.
ReplyDeleteI run the DnsServerApp.exe, log in through web browser, go to settings, under "Forwarders" I quick select "OpenDNS (DNS-over-UDP)", then save. I select the "DNS Client" tab, query "This Server" the domain "yahoo.com", click "Resolve" and I get "Error! DnsClient failed to resolve the request: no response from name servers."
What am I doing wrong?
You have configured forwarders correctly. You will need to check the logs to see what went wrong. It should mostly be some network connectivity issue. Do email to let me know if its not fixed.
DeleteSince you are querying 'This Server', it may be so that there is another application listening on port 53 and thus the DNS server could not run on that port. You can follow this blog post to see how to fix this: https://www.hanselman.com/blog/YourComputerIsNotABlackBoxUnderstandingProcessesAndPortsOnWindowsByExploring.aspx
DeleteThanks. Updating the "DNS Server Local Addresses" from specific IP to 0.0.0.0 looks like it fixed it.
DeleteI can make queries on 127.0.0.1, but not the assigned NIC IP address. Firewalls are disabled. Very odd.
DeleteI've tried adding back the NIC IP address, alone and in addition to 0.0.0.0, and all I get from nslookup is "XXXXXXX can't find yahoo.com: Query refused"
DeleteFurther information: In "DNS Server Local Addresses" if I specify only 127.0.0.1 and ::1, then when I query the outside address I get "No response from server". If instead I specify the NIC IP address, or list 0.0.0.0 as the local address, I get "Query refused" from nslookup.
DeleteTo clarify, when "127.0.0.1" or "0.0.0.0" are specified as the listening addresses, DNS queries on the local system to "127.0.0.1" work, but there is no response on from the NIC "10.x.x.x" interface (as expected). When "10.x.x.x" or "0.0.0.0" are specified as the listening addresses, DNS queries to "10.x.x.x" from the local system or other LAN systems to this address receive "Query refused" message. Very odd. This has been tested on Windows 2016 and Windows 10 systems with same result. Firewalls are off.
DeleteFigured it out - refused because "Allow Recursion Only For Private Networks" was checked, and that includes any queries to the NIC IP.
DeleteYou must always have the default values of "0.0.0.0" & "::" in DNS Server Local Addresses unless you have very specific requirement to have the service running only on particular network adapters.
DeleteDo make sure that no other service is using the udp 53 port by running this command "netstat -ano | find ":53". Check logs for errors to get clues.
If your network adapter address is not in private IPv4 range then DNS server will refuse requests when "Allow Recursion Only For Private Networks" is enabled.
Hi is there any way to set up the DNS to use the ultra surf proxy if so what do I need to do it
ReplyDeleteThe server supports HTTP and SOCKS5 proxy. You can setup the proxy in Settings tab on the web portal.
DeleteHi all, Any way to log mac adress ?
ReplyDeleteNope. DNS Server will log only IP address of the client. If you use the DHCP Server, it will log the MAC address.
DeleteOk, Thanks for help
DeleteFor help you can use firewal and remote syslog.
Hello,
ReplyDeleteI just want to ask is there a way to block/allow certain request on user base? For example for normal users facebook.com domain is blocked and for CEO it is allowed
That is not feasible to do. Its best that you run two different DNS servers for this.
Deleteis it possible to block youtube ads before videos?
ReplyDeleteNot sure about this. Most block lists dont have any domain that blocks YT ads.
DeleteThanks for making this software available.
ReplyDeleteI am using this as a DNS proxy for an existing Windows DNS server so I can use DoH or DoT. I notice there seems to be no facility to change the cache operation. Am I right to assume it just caches according to the DNS record's TTL? Is there any way to turn off caching? As I already have caching on the Windows DNS server there is no point to caching the entry twice.
It would also be useful if there was the facility in your software to change the port it listens for DNS requests. Then I could run your DNS software and the windows DNS server on the same server rather than having to run your software on a different server.
Thanks for the feedback. There is no option to disable cache as cache is critical for any DNS server to operate. Its how it remembers name servers for all the domain names that have been found, remembers which query to not resolve using negative caching, and also does cache prefetching and auto prefetching for faster response times. It also implements serve-stale caching to be resilient to auth server failures.
DeleteThe next release will have option to configure port along with the local addresses to bind to. Next release is expected to be available in a few weeks from now.
Thanks for the reply. I understand the importance of caching but as I am effectively using two DNS servers there seems to be no point in them both caching results and it makes fault finding more difficult if there are two caches withing the same network. I've resolved the issue by disabling the Windows Server DNS cache.
ReplyDeleteI look forward to the next release then I can have all DNS services running on one server rather than split across two.
Keep up the good work!
When I create an A record for local server, there is the option to "Add reverse (PTR) record". When I hit save, I get "Error! No reverse zone available to add PTR record". How do I create the reverse zone? I don't see it as an option. Google had been very little help, Thanks.
ReplyDeleteYou need to create a reverse zone first to be able to add a reverse record while adding the A record. The next version that is under development will add another checkbox to allow automatic creation of the reverse zone.
ReplyDeleteFor now, if your network is 192.168.1.0/24 then just go to Zones, click Add Zone, type in the network address and the reverse zone '1.168.192.in-addr.arpa' will get created automatically.
How will the DNS server decide which Forwarder to use?
ReplyDeleteis it round robin or does it find the quickest over time?
Thanks for asking. The DNS server sends request to all the forwarders that are configured concurrently. The fastest response from any of them wins and is used by the server to respond and cache.
Deletecan I mix TLS and UDP forwarders ?
ReplyDeleteYou must not mix protocols. It will defeat the purpose of using encrypted DNS protocol in the first place so the forwarder options in the GUI does not allow it.
DeleteCan we import a hosts file to the zones? I have quite a long host-to-ip list, and don't want to type them one by one.
ReplyDeleteAnd is this possible in the zones?
sub1.example.com -> 192.168.0.1
sub2.example.com -> 192.168.0.2
Any other xx.example.com -> forward to upstream server like cloudflare
There is no option to import the hosts file into zones. You will have to write some script and use the DNS server's HTTP API to add those records into zones.
DeleteHi, what's the difference between DoH and DoH (JSON)? Is there a performance or privacy benefit of using one over the other?
ReplyDeleteDoH is the standard protocol defined in RFC 8484 while DoH (JSON) is non standard HTTP API developed by Google (https://developers.google.com/speed/public-dns/docs/doh/json). Using DoH which is a standard is always recommended since it will support all DNS standards correctly.
DeleteIve been using technitium for some time as a casual user to block some of the adverts and possibly provided some privacy as ISPs record all web access in the UK. I cant recall why I originally selected DNS-over-HTTPS (JSON) but it either no longer works or is somehow being blocked by Virgin Media in the UK. It was working fine for ages now I just get "DNS_PROBE_FINISHED_BAD_CONFIG" when trying to browse even if I switch from cloudflare to one of the other providers.
ReplyDeleteIt would be interesting to know if it still works for anyone else, I suspect its virgin that are blocking it why I dont know unless its easier for them to inspect the TLS or HTPPS traffic than the JSON.
DoH (JSON) and just the standard DoH both use TLS to encrypt data and only the request/response formats are different. DoH (JSON) is no a proper standard protocol and many DNS providers have stopped supporting it. You should just try to switch to standard DoH protocol and check if that works or switch to a different DNS provider with DoH.
DeleteThanks Shreyas; it just seemed suspicious that when the Cloudflare json stopped working the other providers that had json as an option didnt work either so I assumed my ISP was probably doing something, both the DNS over TLS and DNS over HTTPS (non json) continue to work.
DeleteOn a seperate note I read somewhere that TLS was more secure than using the https option but neither are secure from your ISP without using the VPN option which Im not using I'm not sure how true that is.
Cloudflare has stopped support for the DoH JSON protocol. So, you have to switch to the standard DoH protocol. You can test this independently using the DNS Client tool in the DNS web panel or from the dnsclient.net website.
DeleteSince DoT/DoH are encrypted DNS protocols, your ISP cannot see what request/response are being transmitted so they cannot block only a specific protocol since they cannot know what data is being sent.
DoT and DoH both use TLS to transport DNS requests so there is absolutely no difference between them with regards to privacy and security.
I'm using the adware, malware and tracking block lists are there any lists anywhere equivalent to the IWF list where illegal content can be blocked without blocking normal adult content? It would be good if the IWF list was available as an option for safeguarding but its only available to members and costs at least 1k per annum so thats not going to happen for a free service like technium.
ReplyDeleteI don't keep track of various block lists but you can find some here: https://firebog.net/
DeleteThere are many such sites that maintain block lists that you can search for.
I've notice that compared to Pi-hole, Technitium imports less domains to it's blocklist. My best guess is it's because of comments or other on the same line as the domain address. For example the list "https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt" imports 0 domains. I'm currently using around 45 blocklists and the difference between pi-hole and technitium is half a million domains. Could domain detection be improved in the next version?
DeleteThanks for the feedback. When you have more than one block lists configured, there are a lot of domain names that are common between lists. Technitium loads only unique domain names from all of the lists so the count is the unique domain names that are blocked and not the sum of all domain names in all lists.
DeleteThe other list URL that you mentioned is not getting parsed since the format is not what was expected. The "#" comment symbol in each line is causing the parser to ignore the line. I will get the parser updated to detect this. An update that is scheduled will contain this fix.
Thank you! Looking forward to the update!
DeleteSome Google services such as https://developers.google.com are blocked in our country. To remove this restriction, I use a VPN service, but Google recognizes that this request was sent from a restricted country.
ReplyDeleteI used Technitium DNS Server and entered the IP in the VPN in the DNS field, but again Google noticed and blocked it.
How can I make it impossible for Google to track requests using Technitium DNS Server?
Thanks for asking. It is more likely that Google is tracking you via the Google Account that you have logged into or using cookies. When you use VPN to exit your internet traffic via another country altogether, this is the most likely thing that is happening. This cannot be fixed by a DNS solution.
DeletePassing by to thank the developer and all of the support.
ReplyDeleteI'm using dns on my isp with 200 clients, so far so good.
Passing by to thank the developer and all of the support.
ReplyDeleteI'm using dns on my isp with 200 clients, so far so good.
You're welcome. Thanks for the feedback.
DeleteThanks for asking. Just put this URL "https://family.cloudflare-dns.com/dns-query" in there and it will work.
ReplyDeleteYou can also put in the IP addresses in the round brackets so that the DNS server does not have to resolve the IP address frequently. So you can use the config as below:
https://family.cloudflare-dns.com/dns-query (1.1.1.3)
https://family.cloudflare-dns.com/dns-query (1.0.0.3)
Refer to this page for more info: https://developers.cloudflare.com/1.1.1.1/setup/#dns-over-https-doh
Thanks. I wasn't sure the the parenthetical IP addresses were being parsed or not.
ReplyDeleteAnyhow, for my purposes (malware filtering only) the lines would actually be, per your cited Cloudflare link:
https://security.cloudflare-dns.com/dns-query (1.1.1.2)
https://security.cloudflare-dns.com/dns-query (1.0.0.2)
And the port ":853" -- include that, too?
You don't have to add ":853". That port is used by DNS-over-TLS.
ReplyDeleteThings seem to be pretty much working now, though a few issues remain:
ReplyDelete1. My local, custom blocklist seems to be ignored, although the other, on-lines ones I listed are evidently working. In creating my BL, I used the Adblock syntax; e.g.,
! comment
||www.foobar.org^
, and specified its location in Technitium as
file:///D:/Web/MyBlockList.txt
Look good so far? Perhaps "file:///" wasn't the right way to reference it?
2. In updating my Windows 10 network settings, I was able to set my preferred (127.0.0.1) and alternate (1.1.1.2) ipv4 DNS server addresses, but with ipv6 only the preferred (::1): it refused to save 2606:4700:4700::1112 (or 2606:4700:4700::1002) as the alternate. Any idea why?
3. In Firefox, I changed my DoH provider from Cloudflare to "Custom" (::1). That correct?
Thanks again!
Update: I was able to save my alternate ipv6 address by using the dialog under Control Panel rather than the one under Setting. Windows, oy vey!
ReplyDeleteFor custom block list, you can use the path "http://localhost:5380/blocklist.txt" where the blocklist.txt file will be inside the "config/www" folder which is where you have installed the DNS server. The "file://" path wont work here.
ReplyDeleteDo not use any other DNS server as secondary as it will be counterproductive. Some of the domains which you wish to block may get resolved via the secondary DNS server. Use the DNS server's system tray app to change your network's DNS servers as it will do it accurately without any issues.
For Firefox config, don't configure DoH provider since you have the DNS server running locally. By default the Firefox DNS requests will be served by your local DNS server so you don't have to do anything.
Hmm, www is not a subfolder I see under config (in my Technitium folder); should I go ahead and create it? On the other hand, there is a config\blocklists -- maybe there?
ReplyDeleteUnfortunately, I'm not seeing a Technitium icon in the system tray. Do I need to configure something for that to work? I would indeed strongly prefer to have it running as a Windows service, ultimately, rather than clicking on a shortcut to DnsServerApp.exe to start it up. (FWIW, I installed the portable version, not the Windows installer one. Is the tray app / service found only in the former?)
Meanwhile, I'll go ahead and disable the DoH option altogether in Firefox.
I mentioned the folder path incorrectly in previous comment. You should find the "www" folder in the same folder that you have the "config" folder. The "www" folder contains the web app that you use to access the DNS server's web panel.
DeleteYou should use the Windows installer that is available for download. The installer will create a windows service and also includes the system tray app.
works with this configuration
DeleteHi, I have configured the forwarders to be 8.8.8.8 and the forwarder protocol to be DNS-over-UDP (default).
ReplyDeleteThen I executed the command "nslookup www.google.com {my-dns-server-ip}" and received the response "UnKnown www.google.com: Query refused."
It seems like the forwarders are not functioning correctly.
I would like to inquire whether I misunderstood the meaning of forwarders or if I missed any other settings.
Your forwarder config is correct. Have you changed anything in the Settings > Recursion option to deny recursion? Make sure you have the "Allow Recursion Only For Private Networks (default)" option selected there. Even then if it is not working then are you using public IP address in your network? If yes then use the "Allow Recursion" option to fix this.
DeleteThank you for your response.
DeleteI adjusted the Recursion option, and it worked successfully.
Thank you so much.
Hi there! Is it feasible to opt out of using public forwarders? What would occur if I select "None" from the forwarder drop-down menu?
ReplyDeleteYes. If you do not set any forwarder in there then the DNS server will perform recursive resolution by itself to resolve all requests.
DeleteIs it possible to place more than one Forwarders (DOH and DOT) and make simultaneous queries?
ReplyDeleteYes, this feature already exists. Just add more than one forwarder and set the forwarder concurrency option which is set default to 2 (i.e. 2 concurrent queries).
DeleteUpdate tutorial, please!!!
ReplyDeleteThis blog post is still accurate and so no need to update it.
DeleteHi! I have configured my router to use Technitium as DNS, everything is working smoothly with my PCs, but I have no clue why Android phones connected to my network are not, even when I know are using the router's DNS. Any idea? Thanks!
ReplyDeleteMay be they are using private DNS. Check the settings once. Another thing, instead of configuring DNS on router's WAN settings, you should configure it in its DHCP server settings so that all clients get the IP of your DNS server instead of your router and that you see individual clients on the DNS server dashboard instead of your router's IP.
DeleteHi!
ReplyDeleteI've setup the dns server as per your blog posts for a single zone, the server itself sits on a private network with a vpn gateway, although the dns server itself has permissions to reach to the outside world. The dns provides a single zone for use on the private vpn network, and the setup works perfectly (the machines on the vpn can resolve the other machines on the private network)!
However, I would like machines on the vpn network to be able to resolve addresses externally (e.g. google.com) (for the machines that have external access from the private network)
How do I setup the dns to forward all non zone (non vpn network) requests to (for example) cloudflare dns or google dns?
(I tried the setup above, but it doesn't work -- if I attempt to ping google.com, I get a temporary resolution failure)
Many thanks,
Jonathan
Thanks for asking. Make sure that you have enabled recursion in Settings > Recursion section on the admin web panel and it should work. There is no other config option for this. If it still does not work then check the DNS logs for any errors. Always use the DNS Client tool available on the admin panel for tests and do not use commands like ping for it since you will get detailed info from the DNS Client output.
DeleteThanks for coming back to me, I have recursion set to:
DeleteAllow Recursion Only For Private Networks (default)
I thought that was correct since I don't want people outside the vpn resolving names inside the vpn
The default option will work only for clients that have private IP addresses. Check if your clients are reaching the DNS server with private IP.
DeleteTest resolving any domain name using the DNS Client tool on the admin panel. Also, check the DNS logs for errors.
Thank you for your help. Turned out we had the dns server on the wrong firewall so it was blocking the external calls - it's all working perfectly now.
DeleteI'll send some money to your Patreon as this is an excellent product
You're welcome. Good to know that you found the issue. Thanks for considering to contribute towards the project.
DeleteHi there
ReplyDeleteAre there any known issues with Technitium DNS server and the TP link Deco mesh WiFi units? I have an instance of Technitium DNS running on a raspberry Pi 4b. It's working successfully for my wired clients however anything connecting in via the TP link Deco Wifi has issues with dropping the connection and returning the error "Connected without Internet". ChatGPT suggested that URLs used for connectivity checks (eg connectivitycheck.android.com) from the Deco might be being blocked but this isn't the case. When I query the logs connectivity check URLs resolve fine without issue. I whitelisted them in Technitium admin anyway, just because I could. When that didn't work I turned off blocking all together. Recursion was "allow from private" but changed to just "allow" still no difference. Technitium is performing DHCP and fowarding unencrypted DNS requests to Google's public DNS servers. Any advice would be appreciated, thanks!
Hi there
ReplyDeleteAre there any known issues with Technitium DNS server and the TP link Deco mesh WiFi units? I have an instance of Technitium DNS running on a raspberry Pi 4b. It's working successfully for my wired clients however anything connecting in via the TP link Deco Wifi has issues with dropping the connection and returning the error "Connected without Internet". ChatGPT suggested that URLs used for connectivity checks (eg connectivitycheck.android.com) from the Deco might be being blocked but this isn't the case. When I query the logs connectivity check URLs resolve fine without issue. I whitelisted them in Technitium admin anyway, just because I could. When that didn't work I turned off blocking all together. Recursion was "allow from private" but changed to just "allow" still no difference. Technitium is performing DHCP and forwarding unencrypted DNS requests to Google's public DNS servers. Any advice would be appreciated, thanks!
Thanks for asking. Some mesh routers have option to hijack DNS request by default enabled. It could be that your wifi user DNS request are getting hijack and thus not reaching the DNS server causing this issue. I would suggest that you check all options on the wifi router's admin panel once.
DeletePor favor, atualize a página!
ReplyDeleteIf i use any of these forwarders, are the DNS requests still be done in my home network and then "proxied" over the forwarders, or do i use the DNS Servers from the forwarders if i activate them to use? (Like DoT/DoH etc.)
ReplyDeleteBecause when i use the forwarders, i could simply put the ip addresses from their servers into my devices, without installing technitium.
Is this right, or am i thinking wrong?
Thanks for asking. When you configure forwarders on the DNS server, it will query them only when it does not have any answer available in its cache. So, if one client asks for example.com, it will fetch it from forwarder and cache it. When other clients on the network ask for the same domain, it gets answered from cache which will work really fast.
DeleteWith a local DNS server, you can configure block lists of your choice and block ads/malware from your entire network. You can also configure local LAN zones so that you can access local resources using names instead of IP address. These are things you can do only with a local DNS server.
Thank you for explaining :)
DeleteHello, theres one feature missing, why I am still staying in AdGuard Home:
ReplyDeletebloking services with just one click, choose, Facebook, Instagram or whatever, click it, save it, and its blocked. if this could be implemented, I would immediately switch.
Thanks
Marcel
Thanks for the comment. AdGuard is an "ad blocking DNS server" whereas Technitium is "DNS server with ad blocking as one of its features". Both software have been designed for different purposes. Also, the AdGuard feature requires frequent maintenance, i.e. to maintain list of domain names for each catagory/service to block which can be done only if there are people hired to do this job on regular basis which is possible since it backed by a large company. Technitium DNS server on the other hand is open source app developed by a single person (myself) and its really not feasible to maintain such a feature on regular basis.
DeleteHello, great tool! Looks really promising, the usage of Cloudflare DNs through TOR, absolutely unique!
ReplyDeleteWhat still hold me back: On Adguard home, I can with one click full service, facebook, Instagra, Tiktok, etc,..
Could we implement this here too?
Thanks
Marcel