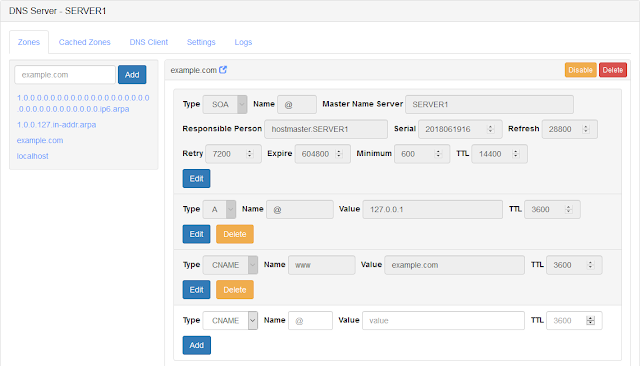
With the release of Technitium DNS Server version 1.3 which adds support for DNS-over-TLS & DNS-over-HTTPS forwarders, it is now a good solution to be used by anyone concerned with privacy & security for domain name resolution on their Internet connection for Windows 10, Linux or macOS.
If you are not clear about what DNS is then read on. Domain Name System (DNS) is a decentralized system that allows you to find out the Internet Protocol (IP) address of any website (like www.technitium.com). So, when you enter a website domain name into your web browser, the web browser uses DNS to find out the IP address of that website. Once the IP address is known, the web browser can then connect to the web server on that IP address using TCP/IP protocols and download webpages and other embedded resources to display on to your screen. DNS servers don't just store IP address records but also store different types of records like mail exchange (MX) records which tell email servers where to deliver email for the recipient user of a given domain.
DNS servers and client use UDP or TCP protocol to exchange requests and responses which are not encrypted. This allows anyone on the network to see those requests and even hijack requests by sending back spoofed responses. There have been many instances reported in media of DNS hijacking done by malware, hacked home wifi routers or even by many Internet Service Providers (ISPs). ISPs in certain places have been found to redirect users to "custom" search pages instead of Google Search or even blatantly injecting Ads on websites that are not using HTTPS security. In some countries, ISPs often use their DNS servers to block websites to enforce government censorship orders.
To mitigate these issues, DNS-over-TLS and DNS-over-HTTPS protocols have been developed and are currently available to be used by a few DNS providers notably Cloudflare, Google and Quad9. But, currently, no operating system, applications or web browsers have built in support for these protocols.
With Technitium DNS Server installed on your computer (or on your network), you can make all your applications indirectly use these DNS providers with the new secure protocols hiding all your DNS traffic from your ISP. Lets see how to configure the DNS Server to use these services to take control and secure domain name resolution on your computer or private networks.
Technitium DNS Server is not configured out-of-the-box with these settings since you have to make a choice yourself of which DNS provider to use. All public DNS providers have their own privacy policies that you must understand before choosing it.
Cloudflare privacy policy promises that DNS query logs are only maintained for 24 hours with not personally identifiable data. They also promise to not sell the data to 3rd parties.
Google's privacy policy claims to maintain a temporary log for 24 to 48 hours which contains user's full IP address details. And a permanent log which redacts the personally identifiable data. There are no details mentioned how this data is used or whom its shared with.
Quad9's privacy policy promises that they do not keep any logs but, only anonymized statistical data on specific domain names which contains things like domain name, timestamp, geolocation, total hits, etc.
Below is a list of DNS providers grouped by the protocol they support. You can configure one or more DNS providers as forwarders but they must use the same protocol.
DNS-over-TLS protocol providers:
- Cloudflare IPv4 {cloudflare-dns.com (1.1.1.1:853), cloudflare-dns.com (1.0.0.1:853)}
- Cloudflare IPv6 {cloudflare-dns.com ([2606:4700:4700::1111]:853), cloudflare-dns.com ([2606:4700:4700::1001]:853)}
- Google IPv4 {dns.google (8.8.8.8:853), dns.google (8.8.4.4:853)}
- Google IPv6 {dns.google ([2001:4860:4860::8888]:853), dns.google ([2001:4860:4860::8844]:853)}
- Quad9 Secure IPv4 {dns.quad9.net (9.9.9.9:853)}
- Quad9 Secure IPv6 {dns.quad9.net ([2620:fe::fe]:853))
DNS-over-HTTPS protocol providers:
- Cloudflare (https://cloudflare-dns.com/dns-query)
- Google (https://dns.google/dns-query)
- Quad9 Secure (https://dns.quad9.net/dns-query)
DNS-over-HTTPS (JSON) protocol providers:
- Cloudflare (https://cloudflare-dns.com/dns-query)
- Google (https://dns.google/resolve)
- Quad9 Secure (https://dns.quad9.net/dns-query)
To make the configuration quick, easy and error free, there is Quick Select drop down list available which lists all the above options. Just selecting the desired option in the Quick Select list will populate the settings automatically for you.
See these examples below to know how the configuration looks like:
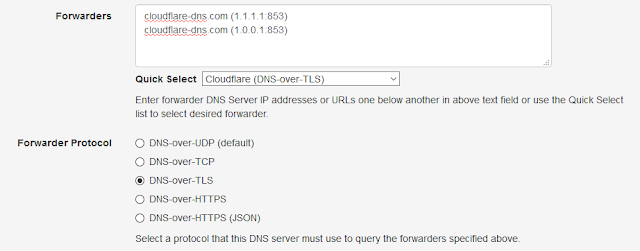 |
| DNS-over-TLS Using Cloudflare |
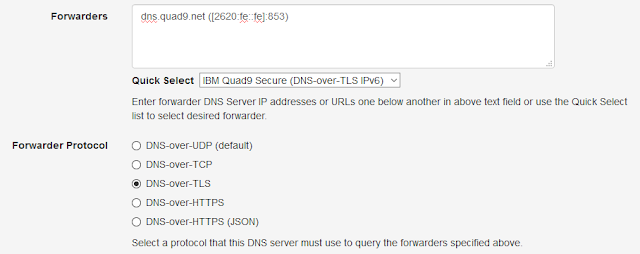 |
| DNS-over-TLS Using Quad9 For IPv6 Internet |
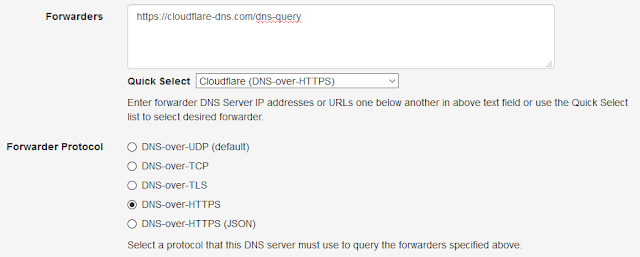 |
| DNS-over-HTTPS Using Cloudflare |
 |
| DNS-over-HTTPS (JSON) Using Google |
As you may have noticed, Cloudflare provides support for all three protocols. Not only that, it is possible to use Cloudflare DNS over Tor hidden service too! Technitium DNS Server v1.3 adds support for configuring proxy server which can of course be made to use Tor running on your computer and use Cloudflare DNS hidden service because WHY NOT?!
You just need to configure dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion hidden service address as forwarder and since all hidden service requests over Tor network are inherently end-to end encrypted, you can use DNS-over-TCP protocol with it. Tor is not included with the software so you will need to install Tor separately and configure it as a SOCKS5 proxy.
This option hides your query from your ISP as well as hides your identity from Cloudflare. But seriously, if you are really that paranoid, just use Tor Browser for all your web browsing.
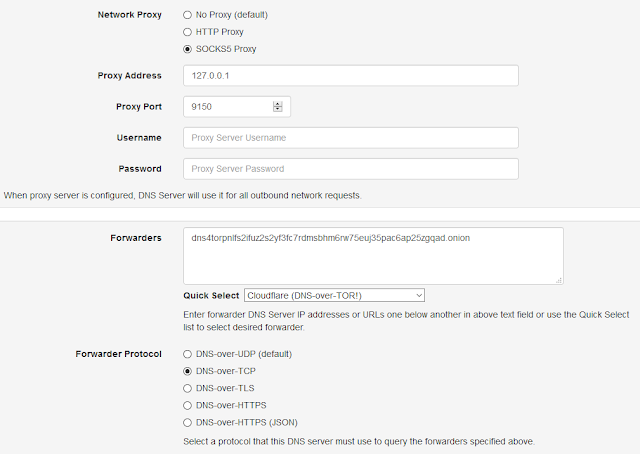 |
| DNS-over-Tor Config For Cloudflare DNS Hidden Service |
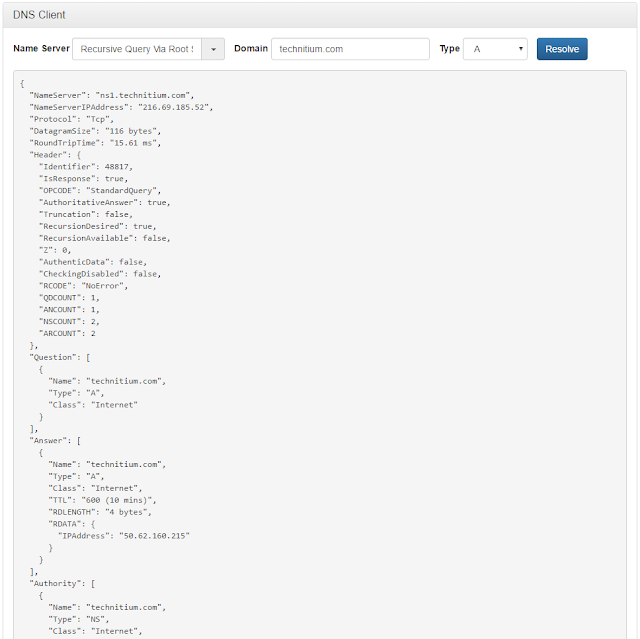
Once you have configured forwarders, make use of the DNS Client on the web console to test the setup by making a test query to "this-server". If everything is configured correctly, you will see the IP address for the test domain you entered inside the "Answers" section of the JSON formatted output.
Finally, to make all your computers and applications to use Technitium DNS Server, you need to configure it on your Ethernet or WiFi network adapter. You just need to setup loopback IP address (127.0.0.1 for IPv4 & ::1 for IPv6) as DNS Server in your network adapter settings as shown below:
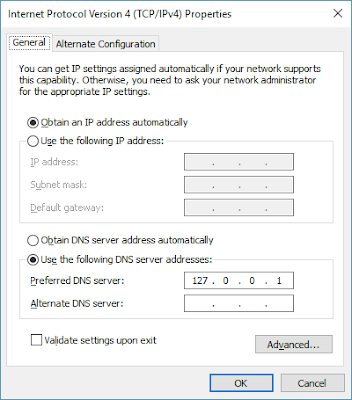 |
| IPv4 DNS Server Network Configuration |
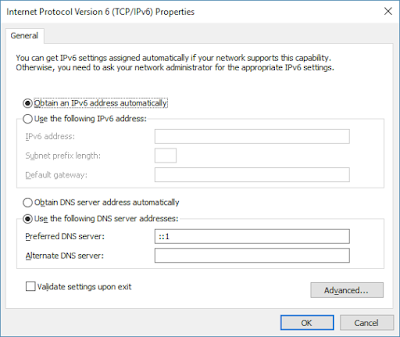 |
| IPv6 DNS Server Network Configuration |
For more queries, write comments below or send an email to support@technitium.com.